I’m a student of the hacker academy. This is one of the modules that we covered in server attacks. Its a smaller part of their ethical hacking course. This module was about brute-force attacks. The hard fact is many people do not understand how brute-force attacks are done, or defended against. Or worse.. Will never see it done to them..
In this guide I will attempt to explain the subject of Brute Force Attacks. Each tool has its pro’s and con’s. I’ll try to cover as many of the main points that i can, but some subjects are outside this documents scope. There are applications that exist in both windows and Linux, but just using it offers little understanding to what the software is doing. This is a very Loud Attack that will get anyone in seven country’s attention.
**Disclaimer : This document should be used as educational material and should not be used on hardware or systems that you do not own or are not authorized in writing to do so on. I take no responsibility for this document or if a monkey beats you in the head with your keyboard while reading it. Its nothing to do with me..
What are the type Brute Force Attacks?
There are 3 basic types of brute-force attacks. Each has its own strengths and weakness’s. And while some attacks may be slow and take a long time to complete, others are faster with more results in less time.
Basic types of Attacks
- Enumeration : Slowest brute force
- Dictionary Attack : List of most likely use passwords for users.
- Hybrid : Combo of Enumeration and Dictionary. Uses word lists but subs variables into word or words.
** Note : Two of the most common and feature rich password cracking or brute forcing tools available to penetration testers are THC-Hydra and Medusa. We will cover these more in the later information.
Systems and Passwords are Changing
Many systems now days ask users to pick fairly complex passwords. Most systems require passwords to be more then 8 characters, but these settings can be changed easily by the user or ignored all together.. When password cracking we start with the minimum length and then crack upwards. Words get longer… Passwords get stranger. Sometimes the passwords is not in our list and time is wasted. When a word is not in our list we can take standard output from one system, such as crunch ( word list generator ) and pipe ( send ) it to the next program as input. Crunch is a great tool for this job.
You can find many commonly used passwords on many site contained as a word-list. Having different word-lists helps to keep your attack focused and on time. Some word-lists are specific to a certain technology, others can be fore a broader set of applications. So lets say default hardware user names and passwords might be in one file. While others might be simple a dictionary of words.
- https://wiki.skullsecurity.org/Passwords
- Kali Has a number of lists that come pre-installed
How to get username’s to try?
Many times companies will betray their users by making the user-name off the email address. This makes it easier for the hacker to identify the account. Before brute-forcing an account, look at the companies website to see if you can get more information to help identify user accounts to try first. People who work in less tech savvy environments are a better target then the network administrator. And might be noticed less then the root or administration accounts, or missed altogether.
Also preform a good recon. Check Facebook, linkedin, or other social sites. I suggest using recong-ng to scrape information from the web to get email address to use.
Website Login cracking with THC Hydra
THC Hydra is password cracking tool. As a matter of fact, i think of it as more of a network logon password cracking tool. A few great features about Hydra are that you can add modules to increase the functionality of this hacking tool, and its very fast at what it does. Hydra also supports multiple network services.
Supported services are: asterisk cisco cisco-enable cvs firebird ftp ftps http[s]-{head|get} http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap[s] irc ldap2[s] ldap3[-{cram|digest}md5][s] mssql mysql nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s] postgres rdp redis rexec rlogin rsh s7-300 sip smb smtp[s] smtp-enum snmp socks5 ssh sshkey teamspeak telnet[s] vmauthd vnc xmpp
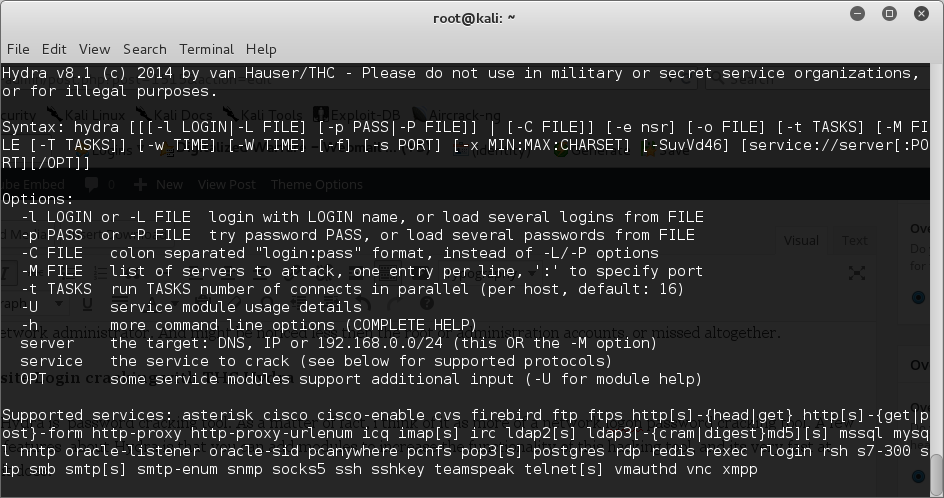
To run with a set username try:
root@kali:~#hydra -l username -p passwordlist.txt target
To run with a list for the username try:
root@kali:~#hydra -L username.txt -p passwordlist.txt target
When using the -l switch, the username can be a single user name, such as “admin”. When using the -L switch username and be a username list. The password list is usually any text file that contains potential passwords. And target can be an IP address and port, or it can be a specific web form field. Although you can use ANY password text file in Hydra, Kali has several built in.
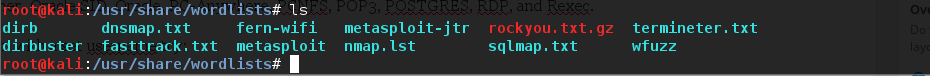
Lets look in /usr/share/wordlists and see what lists we have already
root@kali:~#cd /usr/share/wordlists
Lets list out the contents of this directory:
root@kali:~#ls -al
You can create your own, use these or any word list you download from the web as long as it was created as Linux Friendly and is in the .txt format. Zips and tar.gz files are compressed and will have to be unpacked.
Using Hydra on Web Forms
Using Hydra on web forms adds a level of complexity, but the format is similar except that you need info on the web form parameters that Tamper Data can provide us.
The syntax for using Hydra with a web form is to use <url>:<formparameters>:<failure string> where previously we had used the target IP. We still need a username list and password list.
Probably the most critical of these parameters for web form password hacking is the “failure string”. This is the string that the form returns when the username or password is incorrect. We need to capture this and provide it to Hydra so that Hydra knows when the attempted password is incorrect and can then go to the next attempt.
** Notes : Hydra requires separate copies of word-list in each memory location. Medusa use one copy and gives read only access to threads. So speed is improved as well as memory usage. Medusa is a more stable code base. Hydra tends to crash more. Both support multi OS and multi protocol. Both are able to have custom plug-ins. Medusa Protocols.
Website Form Login cracking with Medusa
Now lets take a look at Medusa. Medusa is a network authentication brute-forcing tool.
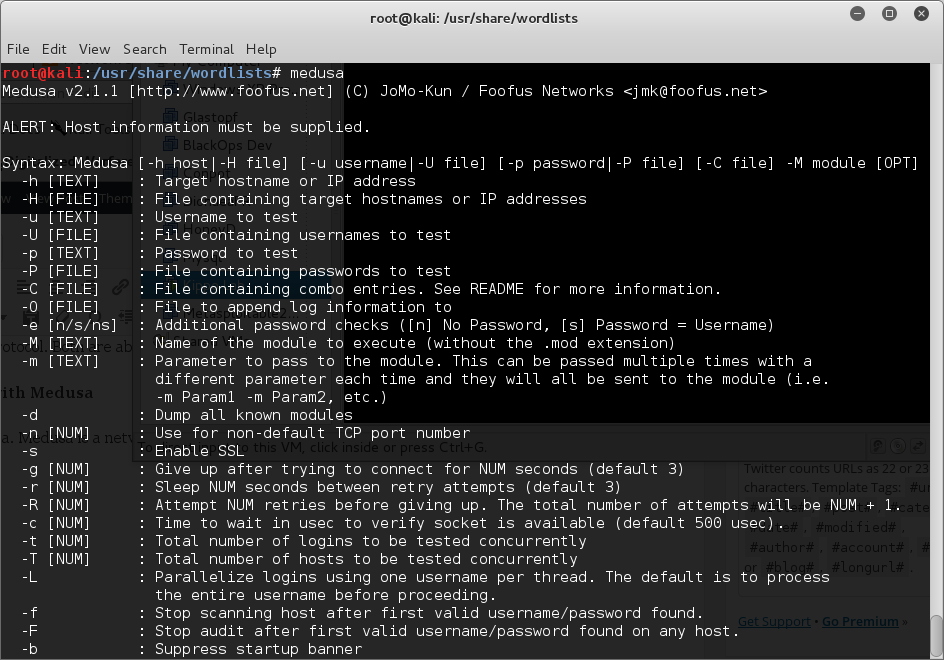 It supports a wide array of protocols
It supports a wide array of protocols
- FTP
- HTTP
- SSH
- SMB
- VNC
- POP3
- IMAP
- MySQL
- Telnet
The factor differentiating Medusa is its capability of testing multiple systems in parallel. Medusa achieves this feat through the multi-threading directive called POSIX Threads, usually referred to as ‘Pthreads‘. When compared to the cost of creating and managing a process, a thread can be created with much less operating system overhead. Managing threads requires fewer system resources than managing processes. Users can specify a list of hosts that are to be tested and Medusa will create a child process for every host and test multiple systems at once leveraging preemptive multitasking to the fullest.
Using Medusa to brute-force a Web Login
- To brute-force HTTP Basic Authentication, we use the following command:
root@kali:~#medusa -h 172.16.1.1 -u admin -P /usr/share/wordlists/rockyou.txt -M HTTP
When Medusa finds a username and password combination that works, it will exit, and display the username and password to the you.







0 comments