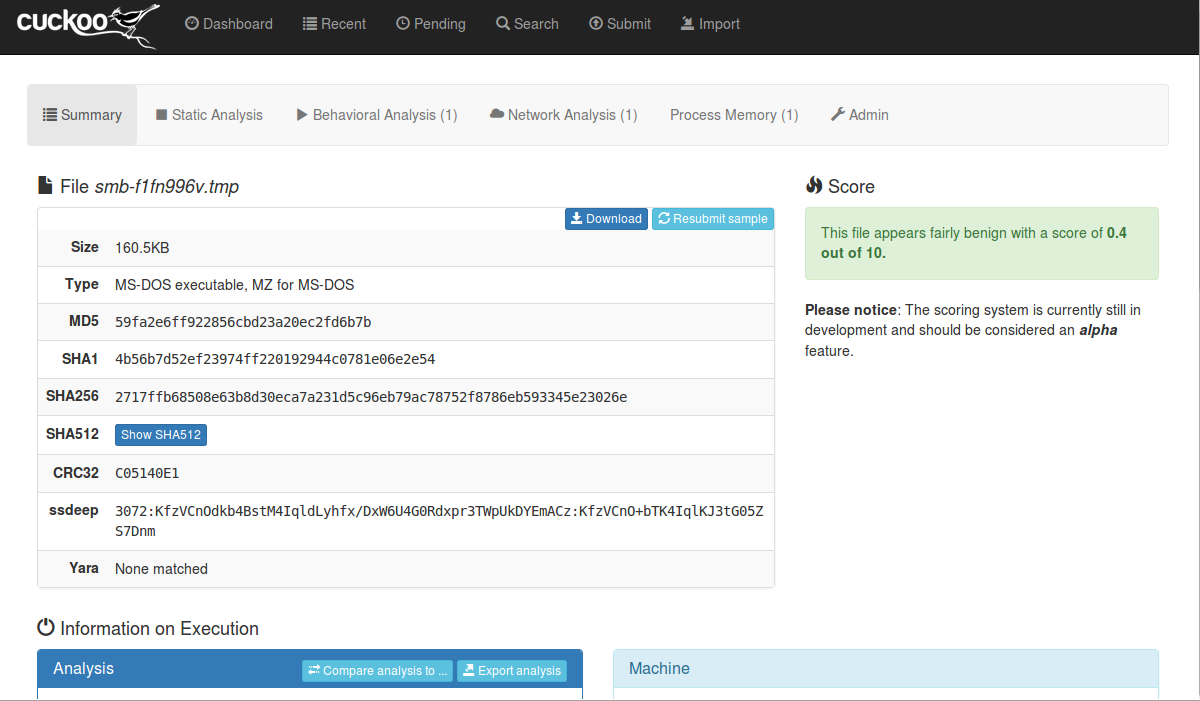
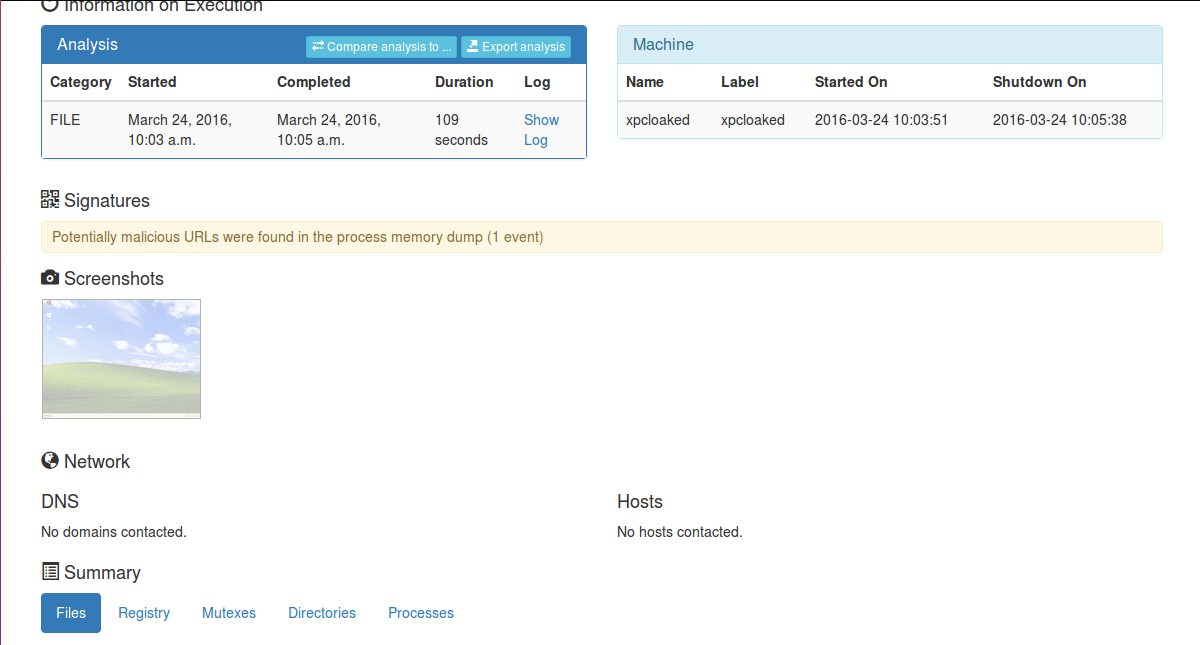
For those familiar with the popular series Star Trek the mind meld is a pretty cool trick. It exposes the mind of the person to be probed and all the deepest secrets known along with some other cool tricks, few of which I know since while it is a wildly popular show, I myself did not follow it. My point is that a social engineer is a great asset to any team but a really good social engineer would be able to do more then trick a low level secretary into reveling her password and undies over snap chat. Some one who could get so far into your psyche that you would knowingly hand over your assets without question is a far more valuable tool and dangerous foe then any simple Jedi trickster. For those of us who wish to bring our game up to a whole new level I present you with not a literal 120 step program but in depth information that will allow you much more control over yourself and thus, those you interact with. This is not going to be a short post since a whole lot of information has to be explained. Please take the time to read my points and learn a thing or two to be a great social engineer.
Some one who could get so far into your psyche that you would knowingly hand over your assets without question is a far more valuable tool and dangerous foe then any simple Jedi trickster. For those of us who wish to bring our game up to a whole new level I present you with not a literal 120 step program but in depth information that will allow you much more control over yourself and thus, those you interact with. This is not going to be a short post since a whole lot of information has to be explained. Please take the time to read my points and learn a thing or two to be a great social engineer.
Before we get too crazy here let me explain that you will not find a simple tactic that works 100% of the time in this post, each person you will encounter will have different levels of different tells and knowing all the possibilities of each will allow us to better do what every social engineer must do. Guess the advisory’s feelings towards you so that you may change tactics before you hit a brick wall. These observations come from my life’s work of studying people. I am above all an observer, someone who watch’s interactions between people and groups while challenging myself to interpret each signs significance. I have read many books and practiced daily so while I am very confident on the correctness of my methods and observations, I am in no way saying that the information presented is 100% across all boundaries. Case in point, a variable that will need to be addressed is something as strange as comfortable talking distance. An American has a higher chance of feeling uncomfortable by you being close to them then say a Japanese national simply because of culture differences. Keeping this in mind will make it easier for you to inadvertently come off as rude for being too close, or too far away from the person you are talking to. While stereotyping is generally a very bad idea when you are trying to make friends or hire someone, it is your best bet when trying to profile someone as quickly as possible, filling and altering the opinion as you learn more about them.
Getting to know someone
 While you are essentially judging your target you are doing so with as much of an educated guess as possible. These tells allows us to alter a judgment and refine our understanding of our target. For instance. If you were yelling at me to get into your car, I would judge the situation different if the setting was outside, at night, and in a dark alley then if we were say, outside a noisy night club. While it may seem obvious, it is because the example was made to be so, many times we need to go over our assessment to ensure that we are taking in all possible variables. In predicting someone’s attack surface its best to consider the following 7 points so that your first impression of your target is well informed. There are over 700,000 distinct physical signs given off by the human body we need to keep track of, 1000 are body postures, 5000 hand gestures, 250000 are facial expressions. We have to make sure we take in everything about the person we are talking to.
While you are essentially judging your target you are doing so with as much of an educated guess as possible. These tells allows us to alter a judgment and refine our understanding of our target. For instance. If you were yelling at me to get into your car, I would judge the situation different if the setting was outside, at night, and in a dark alley then if we were say, outside a noisy night club. While it may seem obvious, it is because the example was made to be so, many times we need to go over our assessment to ensure that we are taking in all possible variables. In predicting someone’s attack surface its best to consider the following 7 points so that your first impression of your target is well informed. There are over 700,000 distinct physical signs given off by the human body we need to keep track of, 1000 are body postures, 5000 hand gestures, 250000 are facial expressions. We have to make sure we take in everything about the person we are talking to.
- Personal Appearance
- Voice
- Body Language
- Actions
- Communication Style
- Environment
- Content of communication
When you are engaging your target try to stay away from the following influences as not doing so gives the target the chance to create the answers we are looking for and causing us to guess wrong or interpret wrong.
- Emotional / Commitment
- Neediness
- Fear
- Defensiveness
By keeping these feelings out of your statements you will be able to form questions that are more informative and less judgmental. When you are “interviewing” someone make sure you set the mood for them to be as informative as possible. Since ANY distraction is a potential interruption and interruptions are conversation killers try to keep you target engaged in conversation. Never interrupt, condemn, argue or patronize your target since that judgment can lead to the target injecting tells and false information to protect their pride. Be empathetic, involved yet not overly so, stay comfortably close to your target and answer with “Right” or “I understand”. Be aware of your body language and stay away from giving off tells that may be picked up and give away your true motives; never get too familiar too fast when talking about yourself so that you can return as quickly as possible to the target. Listen with all your senses and if possible always in person so that you have control of the environment. Listen on their turf and somewhere they feel comfortable while avoiding an audience. Go slow and easy, the best answers come when you don’t allow somebody too long to ponder the possible replies. Think ahead of some questions that you want to ask but don’t be afraid to improvise also. Questions should generally start in these categories: compassion, socio-economic background, satisfaction with life.
A good beginning lineup would be, Where were you born?, What do you do for a living?, Do you belong to any organizations?, What are your goals in the next 5 years.
Try to remove physical obstacles between you and your target so that they feel more closely connected and part of the conversation. Most importantly consider the context of the conversation. If the target is often exaggerating or misquoting others then its best to interpret the information under that context. In general there are three types of questions
- Open Ended – No suggestion on what you may want the answer to your question to be.
- Leading – Same as open ended but with a restricted scope to elicit a response you are looking for.
- Argumentative – Dangerous but can force someone into a reluctant admission.
Using these 3 types of questions one can craft a great line of questioning that will lead to hopefully the information you are seeking. Don’t forget that after each question you should ask good follow up questions to ensure the information you are getting is as clear to you as possible. You may rephrase your last question or if needed completely repeat it with emphasis on certain words you want your target to concentrate on.
Discovering Patterns
As I have mentioned before there is no silver bullet in character development but knowing what the tally is at the end of an evaluation will help you understand that person that much more. When undergoing the character development stage of an interview make sure to note things down so that you can keep track if said trait changes or is altered in an attempt to change your personal picture of the target. Keep the following in mind when you first meet someone to get the most information from each additional meeting.
- Persons most striking traits, and is it consistent?
- Consider each characteristic in light of the circumstances.
- Look for extremes
- I.D. deviations from the learned pattern of the individual your targeting.
- Is the individuals state of mind temporary or a permanent one.
- Distinguish between elective and non-elective traits.
- Give special attention to certain highly predictive traits.
When you first meet someone new, take notes, mental or otherwise of the two or three characteristics that stand out to you the most. To be able to accurately identify patterns in peoples traits and behaviors you need to consider the “stage” upon which they act. Note each change in a person as the settings change and they become more comfortable around you. The significance of nearly EVERY trait depends directly on how big,small , intense or subtle it is. Anything unusual is usually important in understanding people. Ask yourself, is the clue I am evaluating just an isolated event or have I seen this before. Someone’s level of compassion, socioeconomic background, and satisfaction with life almost always revel most about a person so try to touch on each when in a conversation.
Clothing, Jewelry, Mannerisms, Tattoos, Makeup
Sex, Age, Race, Body, Handicaps
First Impressions
Personal Appearance
 Of all the methods available the first impression is the least reliable but it is where we all must begin. Look for consistent combinations of clues, they will be there if your on the right track. Someone wearing inappropriate clothing, makeup, using inappropriate gestures and hairstyles can reflect many things so try not to allow one bias override all others.
Of all the methods available the first impression is the least reliable but it is where we all must begin. Look for consistent combinations of clues, they will be there if your on the right track. Someone wearing inappropriate clothing, makeup, using inappropriate gestures and hairstyles can reflect many things so try not to allow one bias override all others.
Body Language
Involuntary body language may be the ONLY sign of negative traits or emotions. Pay special attention to inappropriate actions. Look for anything that is peculiar or peculiarly unique. Consistency is one key to interrupting body language so make sure they match the person before relying heavily on them. As you will see many signs will show up in multiple categories and you must be able to use all the clues you collect to decipher just which sign the speaker is conveying. Keep in mind that if a person is not lying their manner will not change significantly or abruptly. People who are bored will usually distort themselves physically. Defensive people close up. Make sure you do not misinterpret boredom as surrender or frustration. Someone who is nervous will need an outlet for this nervous energy.
Psychological Profile of someone deceiving.
- Humans see the world as a reflection of ourselves. If consistently accused be weary.
- Is person focused internally or externally ? Confident people are more interested in you understanding not how they appear.
- Point of view of third part is often missing
- Leaves out negative aspects
- Willingly answers questions but asks none back
Signs of Dishonesty. (Honesty would be opposite signs)
- Shifty or wandering eyes
- Change in voice
- Rapid Speech
- Any type of fidgeting
- Shifting back and forth on ones feet or in a chair.
- Any signs of nervousness
- Exaggerated version of the “sincere, furrowed brow” look
- Sweating, shaking or licking lips
- Any activity that obscures the eyes, face or mouth.
- Running ones tongue over the teeth.
- Leaning forward
- Inappropriate familiarity such as invading your personal space.
Signs of Attentiveness / Pensiveness
- Maintaining strong eye contact
- Gazing steadily a an object
- General stillness
- tilting or cocking ones head
- Chewing ones lip/pencil
- Furrowing one’s brow
- Folding ones arms and staring into space
- Leaning back in ones chair
- Looking upward
- Scratching ones head
- Holding ones head in ones hand
- Resting ones head on the hands/fingers.
Boredom
- Letting ones eyes wander
- Gazing into the distance
- Glancing at watch or other objects
- Sighing Heavily
- Yawning
- Crossing and uncrossing legs & arms
- Tapping fingers or feet
- Twiddling thumbs
- Pointing ones body away
- Shifting weight
- Leaning forward and backward in ones chair
- Rolling the eyes
- Moving ones head from side to side
- Stretching
- Cradling ones chin in hand
- Picking at things (clothes, shoes, ring, etc)
- Attempting to do another task
Anger / Hostility
- Arms, legs, ankles crossed
- Short or rapid breath
- Frequent reputation of certain phrases
- Finger pointing
- Rapid speech
- Rapid body motions
- Tightly closed lips
- Stiff, rigid posture
- Shaking
- False / Sarcastic laughter
- Frozen expression / scowl
Frustration / Confrontational
- Frequent eye contact
- Within your personal space
- Gesturing with hands
- Shrugging or pointing
Surrender / Total Surrender
- Sighs
- Grimacing
- Rapid exhaling
- Hands on hips
- Hands on head
- Exaggerated movements
- Rolling / Closing eyes
- Walking Away
- Shaking ones head
- Shrugging
Depression
- Isolation from social contact
- Poor concentration
- Inability to focus or plan ahead
- Low / Quiet speech
- Downcast eyes
- Slow and deliberate movements
- Change in appetite (either under or over eating)
- Forgetfulness
- Inattention to hygiene or dress
Grief / Sorrow
- Tears
- Listlessness
- Inability to complete normal daily tasks
- Isolation
- Down cast eyes
- Apathy
- Signs of depression & confusion
- Relaxed facial muscles
- Slumped or slacked body
- Motionlessness or slow movement
Indecision
- Shifting back and forth
- Looking back and forth between objects
- Tilting head from side to side
- Opening and shutting hands or moving one hand then another
- Opening and closing mouth without saying anything
Nervousness
- Eyes darting back and forth
- tensing of the body
- Curling up of the body
- Shifting weight side to side
- Rocking in ones chair
- Crossing / Uncrossing arms/legs
- Tapping hands, fingers, feet
- Adjusting o diddling with objects
- Wringing the hands
- Clearing the throat
- Nervous cough
- Smile tick (a quick smile then back to their normal expression over and over)
- Biting the lip
- Looking down
- Chattering nervously
- Shaking or quaking (Extreme situations)
- Sweating
- Chewing nails or picking cuticles
- Hands in pockets
- Rotating side to side with upper body
- Becoming silent
Voice
 Learn to hear between the lines as every conversation is built from two distinct dialogs. The actual words and the conscious / subconscious vocalization, volume, cadence and tone of voices. To hear the unspoken message focus on the voice not the words in short spurts. Consider if vocal characteristics are voluntary. Listen for patterns and changes as the conversation continues, consider context and the environment. Lastly compare the voice to the body language your picking up and the words being used. Keep the following in mind when interviewing someone since they can be indicators of someone trying to fool you.
Learn to hear between the lines as every conversation is built from two distinct dialogs. The actual words and the conscious / subconscious vocalization, volume, cadence and tone of voices. To hear the unspoken message focus on the voice not the words in short spurts. Consider if vocal characteristics are voluntary. Listen for patterns and changes as the conversation continues, consider context and the environment. Lastly compare the voice to the body language your picking up and the words being used. Keep the following in mind when interviewing someone since they can be indicators of someone trying to fool you.
What is said: Verbal Content
- Uses YOUR words to make a point
- Keeps adding information unit they are sure your sold on the story.
- May stonewall to limit challenges to position held by accuse
- Watch out for Freudian slip
- Depersonalizes answer by offering belief n the subject instead of directly answering.
- Implies an answer but never states it directly
How something is said
- I, we , us are underused pronouns or absent
- Deceitful responses to questions take longer to think up
- Reactions that are all out of proportion to the question
- Speaks in monotones and passive voice.
- Statements sound like questions.
Decoding Vocal Clues
Loud Voice
- Control
- Persuasion
- Compensation for a perceived flaw
- Reaction hearing loss
- Inebriation
Is this voice appropriate? Is the loudness constant or does it vary? How is the voice being used?
Soft Voice
- Can be used to manipulate
- Lacks confidence and assertiveness
- Maybe reflects calm self-assurance
- Arrogance
Does the speaker seem tired? Is the speaker internally forcing someone within ear shot? Is the speaker maybe lying? Is the speaker limiting who can hear?
Rapid Speech
Fast speaking by someone who is usually normal paced can mean
- Nervousness
- Anxiety
- Impatience
- Insecurity
- Excitement
- Fear
- Drugs & Alcohol
- Anger
- Caught in a lie
- Desire to persuade.
Slow Speech
- Anxious
- Ill
- Confused
- Under the influence
- Confused
- Lying
- Deep in thought
- Fatigued
- Sad or grieving
Is slow speech normal or is it discomfort?
Halting Speech
- Insecurity
- Nervousness
- Confusion
- Untruthfulness
- Attempt at precision
Speech patterns in halting speech include pitch, intonation and emphasis, flat, unemotional voice, pretension/snobbery and whining.
Breathiness
- Anger
- Sexual interest
- Disbelief
- Excitement
- Frustration
- Nervousness
Raspy Voice
- Smoking
- Illness
- Gives speech’s
Mumbling (chronic)
- Lack of confidence
- Preoccupation
- Insecurity
- Fatigue
- Anxiety
- Inability to articulate thoughts.
- Self-consciousness
- Illness
Mumbling (unchronic)
- Distracted
- Tired
- Chewing
- Under the influence
Mumblers seldom demonstrate significant leadership ability or even any desire for such control
Accents: May tell you about cultural mannerisms.
Communication Style
In general there are 6 different communication styles, each style tells us a little bit about the person speaking along with some details about who they are vs. who they want us to think they are. On a simple scale from 1 to 6, one is the hardest to communicate with while 6 is the easiest. Here is a quick rundown of each style along with its ranking.
- Nobles – Believe communication is to exchange information ONLY.
- Magistrates – Opinionated, argumentative and difficult to deal with.
- Senator – Chooses whatever communication style works best in the situation.
- Candidates – Seek to communicate along a path of least resistance.
- Socratic – Purpose of communication is to talk. Loves discussion and debate.
- Reflectives – “Touchy feely” people. VERY communicative.
Looking for motive
There are many reasons for manipulative conversations including but not limited to avoid embarrassment, trick someone, avoid hurting other people, cover up a lie, or pull someone into an argument. Manipulative answers can be broken down into 5 categories.
- Non responsiveness – May be avoiding embarrassment, conflict, truth or an emotionally difficult subject.
- Not denying or explaining when expected – Hiding something, wants to avoid conflict, playing “games”, may be offended or trying for control.
- Short answers – May be early signal for dishonesty.
- Long Answers – May be used to hide the truth. Used to avoid lying outright to try and spread the truth about. Is answer candid or incoherent?
- Answering questions with a question – Used if someone doesn’t want to commit to an answer, used to redirect the conversation and may show them as being secretive.
Conversational Detours
The pregnant pause
A pause after you have said something provocative, threatening or off subject catching the other person off guard could mean that you were surprised or offended. A brief pause could mean anger, frustration or disgust. Look closely for clues in the persons face, eyes, and mouth.
Interruptions
Constant or poorly timed interruptions may be motivated by impatience or boredom. Are they trying to control the topic by changing or altering the topic?
Rambling
Rambling usually revels nervousness, confusion, insecurity, a need for attention or . If this is not normal for the individual then it could mean intoxication, severe fatigue or simply distraction.
Changing Subjects
Intention can be gathered by looking at the relationship between the old topic and the new one.
Revealing habits of conversation
Defensive Behaviors
- Withdraw – Grows silent suddenly, pay attention to tone and content.
- Aggressive Attack – Blame someone else or you to excuse or sidestep issue.
- Profess religious beliefs, family values or high morals.
- Emotionally disarm attacker by flattering them with praise.
- Unprovoked protestation of innocence – Really overblown excuses for innocence.
People commonly volunteer information to make a connection with you by telling you what they think you want to hear.
Verbal calling cards
- Slang – Can shed light on cultural influences and social economic background. This includes bad grammar. How and when slang is used is also important.
- Word Themes – The more a person relies on word themes the more strongly he relates to some aspect of those favored words.
- “Aggressive Terms” – Won, battle, out flanked, aggressor.
- “Honesty” – Frankly, to be honest, to tell the truth.
- Use of titles – The way a person uses a tittle can revel his geographic background. I.e. Sir or Ma’am can be a sign that the speaker is from the south or military. Can show or ignore respect and be sarcastic for example changing Dr. Oz’s title to Mr. Oz .
- Profanity – May equal being socially inept, excitable, or insensitive to the reaction to others. If used in anger the person may be seen as aggressive and a volatile temper. Excessive is threating and may be used as intimidation. To gauge profanity consider how often and under what circumstances its used.
- Braggadocio – Takes the form of interjecting ones accomplishments when they are not relevant, name dropping or exaggerating ones success. They always lack true confidence.
- Exaggeration – No room for grey. Signals insecurity and trying to get noticed. Trying to control the conversation and trying to control their true behavior.
- Ingratiating behavior – Blatant manipulation, kissing up, brownnosing, consider the context, may be trying to comfort you or make you feel accepted. May lack confidence. Brownnosers fall into two categories.
- Those who ingratiate to gain personal advantage.
- To win your approval.
- If demeanor, appearance and other clues point to passive then they probably were not trying to manipulate you.
- Self Criticism – If speaker does this more then twice, start to ask “why”. Very insecure and low self esteem. May be looking for support, encouragement, help or you to disagree with them. May be used to put you at ease. How they respond to others remarks is a good test to gauge reasoning.
- The broken record – Either senile or mental issue or nervously filling space in conversation, or sending a loud clear signal that something is on his mind and wants acknowledgement.
- Gossiping – Consider target and context to find motives.
- Humor – Can be sarcastic, subtle, genuine or insincere. Can be a weapon or a shield. Frequently use to disguise true feelings. Used to turn conversation from serious to lighter one. Compassion to show empathy or understanding. Disguise emotions they don’t want to expose.
- Sarcasm – Used to either get a laugh or make a point indirectly
Actions in / with speech
- Words < actions
- Focus on how one behaves towards others.
- We all make mistakes, but not patterns
- People MAY change, ask yourself
- How long is it set?
- How recently has it changed?
- How quickly?
- What could have motivated him?
- Look for patterns – Question ANY time someone deviates from their known pattern.
- Selfishness
- Performance under fire
- Unkempt promises
- Avoidance
- Preaching
- Fanfare
- Spending habits
- Environment
- Read environment with all your senses.
- See the big picture – Clues are everywhere but focus on props, calendars, photos, books, magazines, art, plants, desk or refrigerator props.
- Watch for differences in peoples public vs. private environments.
- Find out where target goes for “me” time.
- Birds of a feather, who we hang with says a lot about how we think.
- Everything about us is effected by our environment
Exceptions to our rules
- Always consider whether your missing something.
- Be alert for:
- The elastic person – time and exposure will show up lies.
- Rehearsed Presentation – remove from comfort zone
- Liars – focus on nothing that he says
- Delusional Thinker – Fool yourselfers
- Physically Disabled – They think and react differently depending on the condition.
- Illness, fatigue and stress
- Drugs and Alcohol – will case changes from one moment to another
- Cultural influences
- Never forget coincidences do happen! Don’t assume too much.
- When listening to your inner voice make sure you review evidence that made you feel your “hunch”
Snap Judgments
Sometimes we have to make our decisions as quickly as possible. With time and practice you will be able to do a pretty decent snap judgment that is pretty close to truth. Please keep in mind that this is something that takes a great amount of concentration to ensure you don’t miss anything that will bias your judgment incorrectly.
A quick way to do such a snap judgment is to follow a simple workflow
- Work from overall picture down to subtle clues.
- Keep I mind the question your trying to answer. No reason to over analyze.
- Zoom in on “key elements”, if you see a unique trait, does it tell you something if you watch closely?
- Look for patterns
- Decide quickly, second guessing yourself can lead to lots of problems!
- Error on the side of caution and practice, practice, practice!
Interpreting Traits
These are probably the most socially arguable part of this method but you will find that tied together with the information collected using the methods already mentioned you will be able to draw some very interesting conclusions quickly.
Complexion
- Tan – outdoors a lot or tanning salons
- Pale – No so outdoorsy, oober skin health, ill or from somewhere with lots of snow and bad weather.
- Irregularities – Facial, maybe they cant afford to remove or don’t care
Hygiene
- Poor hygiene – out of touch, high level of self centeredness, lack of common sense, insensitive, mentally ill, drug use, ill, poor, lazy.
Fastidiousness
- OCD, egotistical, structured, vain, inflexible, unimaginative, concerned about others opinions
Writing, logos and pictures on clothes
- T-shirts with sports insignias – Fan of sport
- Souvenir T-shirt – Traveler or Outdoorsman
- Prominent Designer – Image conscious and may lack confidence.
- Regional style
- Tip off where they are from
- Where they lived or currently live.
- May identify them with that region.
- Cultivated images – May not reflect true inner identity but outward role.
Flamboyance VS Conservativeness
- F = Bright colors, shocking or distinctive styles.
- C = Classic styles, subdued colors, careful and meticulous grooming
- F = Want to stick out generally
- C = want to bend in.
Conservative dressers are generally confident.
Flamboyance – Creative, artistic, imaginative
- Usually not overly “poor” or very practical
- are non conformists and don’t care about opinions as long as they got an audience
- Independent even a bit flaky
Conservativeness
- Are conformists
- Often practical, authoritarian, ad analytical
- Most people are conservative in their thinking habits.
Practicality VS Extravagance
- Practicality – Anything that points to comfort, cost or utility over style
- Extravagance – Simply opposite
Practicality
- At ease with themselves
- Not self-centered
- Willing tot be non conformists
- Frugal
Extravagance
- Image conscious
- Poor self esteem
- Desire acceptance and approval
Sexual Suggestiveness
- Tremendously confident
- Very insecure
- Trying to get attention
- Sexually liberated
- Outgoing, vain, self centered
Dowdiness
- Out of social mainstream
- Insensitive to issues of appearance
- Poor or lower socioeconomic background
- preoccupation elsewhere
- Sloppiness
- Artistic, intellectual or absent minded
- Professor syndrome
Interpreting body language
Arrogance
Preen, glance at themselves, make grand gestures, keep great distance from others, bore easily, make sexual maneuvers and posturer, boast, adopt affections.
Humility
Good listening skills, self-depreciating humor, quiet demeanor, shows courtesies.
Confidence\Leadership
Lead\control conversations, surrounded by peers, volunteer for unpleasant tasks, good listeners, self assured smile, walks with confidence, almost striding. Firm handshake, better dressed, good hygiene, dress appropriately or more expensive, engaging, seldom follows trends, physical and athletic, good eye contact, conservative haircut, erect posture, squares body to talk.
Confusion
Verbal repletion, repetitive motions, signs of indecision or frustration, conflicting or inconsistent behavior, shifting or shuffling
Defensiveness
Crossing arms, legs, and/or ankles, clenching teeth, jaws or lips, averting the eyes, body squared to talker, hands on hips, quick exhaling, closing mouth tightly and refusing to talk. Leaving abruptly
Embarrassment
Turning away, flushing, nervous laughter, avoiding eye contact, shaking ones head, avoiding people, leaving the room.
Fear
Wide open eyes, screaming , blushing, hands over the face, being frozen, gulping and swallowing, looking a around, clutching other objects or hands tighter, hands in front of the body, leaning or shifting backward, turning away, quick, jerky flailing or stretching out of the extremities, shaking, heavy breathing, quick swallow breathing, holding ones breath, walking quickly, stiffness, licking lip, small tentative steps.
Resentment
Stiffening body, powting, crossing arms, grimacing, avoidance, signs of anger.
Secretiveness\Openness
Whispering, set jaws, a guarding posture, covering ones mouth, body turned away, avoiding social interaction, revealing little emotion, brief, mechanical handshake, frequently locks down, looking around when being addressed, removing personal stuff from view.
Openness: Worm smile, kissing on greeting, long eye contact, standing close, firm handshake, enjoying social interactions.
Sexual or Romantic Interest
Exaggerated smile, laughter, staring, winking, wetting lips, thinking, crossing/uncrossing legs, thrusting out chest/hips, walking with swagger or wiggle, primping lounging back, coy smile, flipping hair, personal space invasion, reveling clothing, touching ones clothing, touching object of affection, excessive perfume, makeup or cologne, overdressing, whispering, intent listening, intently looking the other person up and down, isolating ones affection by trying to get them alone.
Suspicion\Disbelief
Suspicion: Furrowed bow, squint in the eyes, turning head slightly down, looking slightly upward, tilting head, tight lips, signs of pensiveness.
Disbelief: Eye-rolling, head shaking, grimacing, frustration, turned up mouth corners, quick teeth exhale.
Worry
repeated action, biting nails, shaking, wringing hands, fidgeting, face rubbing, hands through hair, lack of focus.
Using the provided information above you should be able to reliably and consistently judge a person simply by talking to them. This technique along with knowledge in the field of Information Security would make anyone a dangerous honey pot in of themselves. Please handle with care and never stop learning.