In order to get the fix my ever increase for knowledge calls for I decided to add a malware lab to my development box. The development box is setup to run the tools of my trade which includes a web browser and Notepad++. Anyone developing PHP applications with more is spoiled. So here I have this box loaded with ram and hard disk space which will never be touched if I continue at the rate I am now. So I decided that I might as well add some functionality to it.
When considering what to put on this box (named foxtrot) I needed to know exactly what I needed out of him. I knew I wanted him to be safe in my studies and that I wanted to analyze malware so I needed to ensure I had not only the tools but the network setup. So my check list started.
- Must be on an isolated network.
- Must simulate multiple Operating Systems.
- Must be able to simulate Internet availability so that C&C calls and downloads can happen.
- Must be able to start fresh once analysis is complete.
From that simple list I figured out that simply installing a basic set of Operating Systems and some cool tools I could get EXACTLY what I needed. Here are my answers to the above needs.
- Multiple versions of windows VMs. ( Windows XP, 7, 8.1)
- A Linux VM. ( Debian 8 Jessie )
- Linux Malware Analysis Platform. (Remnux)
- Windows Malware Analysis Platform. (IDA Pro, Wireshark, PeStudio, CaptureBAT, Process Hacker, Regshot etc)
- Simulated Internet. (InetSim)
- VMWare (Snapshots)
Lab Setup
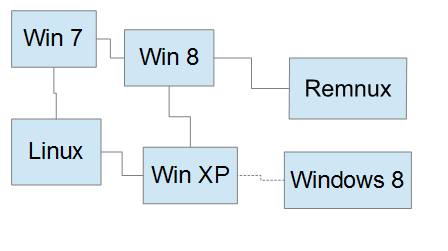 The idea behind this setup is simple in theory. I wanted a full network that included both Windows and Linux environments but I have to keep them on an isolated network. That being said, I also had to have the ability to monitor network traffic and have isolated space to host my tools. I decided that both the Remnux box and the extra Windows 8 box would be just that. Both could be connected/disconnected from the network as needed and together allowed me to host all the tools I would need in a very safe manner.
The idea behind this setup is simple in theory. I wanted a full network that included both Windows and Linux environments but I have to keep them on an isolated network. That being said, I also had to have the ability to monitor network traffic and have isolated space to host my tools. I decided that both the Remnux box and the extra Windows 8 box would be just that. Both could be connected/disconnected from the network as needed and together allowed me to host all the tools I would need in a very safe manner.
Setup / Install
First things first, I need to isolate a network. For my virtual manager I am using Workstation 12 Pro, however just about any VM will do as long as you follow the basics of isolation! So since I am using VMware workstation I will use screenshots of those.
 So once you open the Virtual Network Editor, you can create a new, safe network to connect your VMs to. If you see that the Add Network option is greyed out, make sure your running VMWare as administrator, it needs the permission to create new networks. Click on Add Network and choose an available network (in my case I chose VMnet5), fill out the settings you want and click OK. A bunch of stuff will happen so be patient and the install will go fine. As you can see its a pretty normal network, nothing special about it.
So once you open the Virtual Network Editor, you can create a new, safe network to connect your VMs to. If you see that the Add Network option is greyed out, make sure your running VMWare as administrator, it needs the permission to create new networks. Click on Add Network and choose an available network (in my case I chose VMnet5), fill out the settings you want and click OK. A bunch of stuff will happen so be patient and the install will go fine. As you can see its a pretty normal network, nothing special about it.
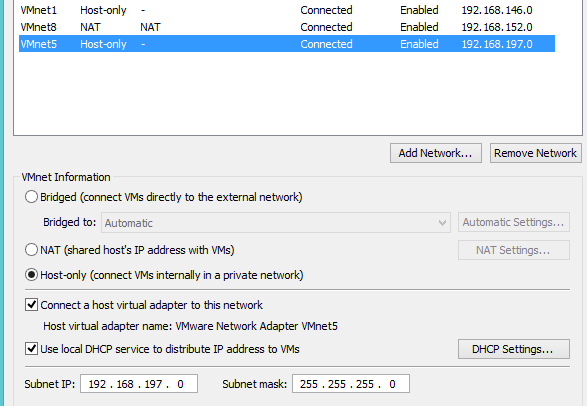 Ensure you have the Host-only clicked, the local DHCP on and the virtual adaptor. The subnet and mask are up to you to choose but ultimately will depend on just how big a virtual network you want to have. Once done, its time to install the Operating System. Keep in mind that NONE of the systems that you plan to have infected should have the guest tools installed, this will limit the chances of your VM being discovered by the malware your studying (this technique is actually becoming less common since so many people now run an operating system in a virtual machine so yay !) and its always best to be safe. When installing your Operating System always make sure that you change the Network Adapter settings to Custom and choose your newly made Host-only network.
Ensure you have the Host-only clicked, the local DHCP on and the virtual adaptor. The subnet and mask are up to you to choose but ultimately will depend on just how big a virtual network you want to have. Once done, its time to install the Operating System. Keep in mind that NONE of the systems that you plan to have infected should have the guest tools installed, this will limit the chances of your VM being discovered by the malware your studying (this technique is actually becoming less common since so many people now run an operating system in a virtual machine so yay !) and its always best to be safe. When installing your Operating System always make sure that you change the Network Adapter settings to Custom and choose your newly made Host-only network. 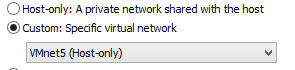 We don’t want these machines all that updated. If you DO want to upgrade you can always upgrade first then switch networks but its not something I would recommend. The more vulnerable your VM boxes the better chance the malware or virus will stick.
We don’t want these machines all that updated. If you DO want to upgrade you can always upgrade first then switch networks but its not something I would recommend. The more vulnerable your VM boxes the better chance the malware or virus will stick.
Once all your Operating Systems are installed its time to move on to installing all the tools. Your going to want to keep your two analyzing boxes up-to-date since you wouldn’t want anything to get ahold of them and your going to want to make sure you have decent firewalls installed. Once done you can spin up your network, ensure they can all talk to each other and then take snapshots to ensure that after each infection you can just revert back to a clean system. 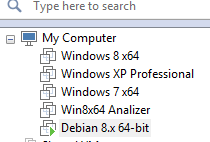 Now just sit back, infect a machine and begin your knowledge quest. Never stop learning!
Now just sit back, infect a machine and begin your knowledge quest. Never stop learning!






0 comments