A denial of service (DoS) attack is a malicious attempt to make a server, service, or another resource unreachable to users, or remote systems. Typically this is done by either sending large amounts of data to the system we want to interrupt. As long as the Data being sent is enough to keep the server, or system from recovering the systems will stay down.
In this guide I will attempt to explain the subject of DDoS. This is a very old attack style that has been around since the Internet has existed, and will always be a valid attack vector. Its attack target’s a flaw that exits at the very core structure of the Internet. Connectivity. If you cannot connect, you cannot get to your resource, as well as your resource cannot get to you. There are applications that exist in both windows and Linux, but offer little understanding to what the software is doing. This is a very Loud Attack that will get anyone in seven country’s attention.
**Disclaimer : This document should be used as educational material and should not be used on hardware or systems that you do not own or are not authorized in writing to do so on. I take no responsibility for this document or if a monkey beats you in the head with your keyboard while reading it. Its nothing to do with me..
What are the Common Types of DDoS Attacks?
The most common type of Denial of Service attack involves flooding the targets with large amounts of external communication requests. These requests, which are specially crafted, overload the systems targeted, and stops it from responding to legitimate traffic, or slows its response so much that it is considered effectively off-line.
What kinds of Devices can be Targets? Computers?
Not all DDoS attacks are against hardware. Some DoS attacks can also target available system resources, such as bandwidth, disk space, CPU time, configuration information. Moreover, a DoS attack can be designed to: max out the processor, preventing usage; trigger errors in machine microcode or sequencing of instructions, forcing the computer into an unstable state; crash the operating system altogether. With the addition of the “IoT” market, this means pretty much everything is fair game.
What are the Differences Between a DoS and a DDoS Attack?
In most cases its the number of computers and the complexity of the attack. In a DoS attack it is most commonly found there is one computer and one server or resource. In a DDoS attack there can be thousands of computers, sometimes called a bot-net, and a few servers, ports or other systems.
What are the Common types used today?
We try to define the different attacking into three main categories.
-
Size or Volume Based Attacks
-
Protocol Based Attacks
-
Application Layer Based Attacks
While SIZE or Volume based attacks may include:
-
UDP floods : Sending data to ports on the machine. When the machine get the request it has to look through its list of programs listening on ports and try to match the request. If it cannot it sends back a ICMP Unreachable Packet..
-
ICMP floods or Ping Floods : Sends massive amounts of ping requests to overload server or resource. Can be one user or a bot-net.
-
spoofed-packet floods : Here we fake the origin of the UDP Packet to keep the attacker machines from receiving the request.
Here the attackers main goal is to exhaust the bandwidth of the server or site. We measure the Attack Size in bps. (bits per second) and by its duration. In recent years we have seen a Increased amount of Data but for lower Durations of Time. As to before Lower Amounts of Data but the attack lasted for days.
There are a few notable types of protocol attacks. They include SYN floods, fragmented packet attacks, Ping of Death,and my favorite…. The Smurf Attack. When we look at these attacks, they use many of the server resources, an other hardware, such as firewalls and load balancers, These attacks are measured in pps. ( Packets per second )
The Smurf Attack : Oh Smurf me!! Smurf’n Server Smurf!!
The Smurf Attack is a very old-school ( around 1998 * Patched Now ) kind of attach that we do not see often. Its like the Perfect Smurfing Storm… By taking advantage of ICMP, and sending a ECHO request to the Server… the server would respond with a response…. The Response was called a ICMP ECHO RESPONSE… By pinging the IP Broadcast Address the Device would forward a copy to any other on the network. And since its a BROADCAST request they will respond to the request. The attacker has forged the ipaddress to his victim ipaddress and all responses will go there. Each machine participates in the DDoS attack by their response.
Fraggle : Similar to Smurf. Uses broadcast to create amplification.
The application layer to me presents the most Dynamic Attack Vector. Some application layer attacks are Slowloris, Zero-day, DDoS attacks that target Apache,Linux, BSD, and Windows. Where each request is a real request, the goal of these attacks is to crash the web server. We measure these attacks in rps. (requests per second)
What Tools are available on the net?
There are a few key tools I will be covering in the following topics. These tools are freely available and I will try to give advice or insight when I can. Please read the documentation on the tool. If you don’t your just cheating yourself out of some really special attack possibility. My machine is stock Kali Linux in all of the following. If I am including video demo the I was using Virtual Box and all attacked were on my own network.
Some of the tools are installed through wget or git. Make sure you have Java installed. Some tools may have been updated since I wrote this, but I hope it covers the basics.
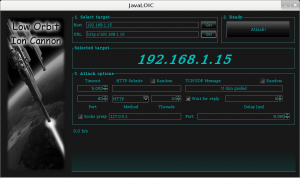
Low Orbiting Ion Cannon : Amass The Army..
LOIC is an application developed by 4Chan-affiliated hackers designed to launch and carry out Distributed Denial of Service (DDoS) attacks on websites or Servers. The idea behind LOIC is that it can allow you to participate in attacks even if you’ve no clue how to hack. Just download a copy of LOIC punch in the target information like a URL or an IP address and your now ready to try and knock something down.
Binary : http://sourceforge.net/projects/loic/files/latest/download
Java : http://sourceforge.net/projects/javaloic/files/latest/download
GitHub Link : https://github.com/NewEraCracker/LOIC/
Follow the step below into install Low Orbiting Ion Cannon into your opt folder. You will need to have Java in order to run it.
My Java Version Info :Java version “1.6.0_34”
- Create folder in /opt called loic : mkdir -p /opt/loic
- Download Java version into /opt/loic
- Set file Executable : chmod +x /opt/loic/JavaLOIC.jar
- Run LOIC : java -jar /opt/loic/JavaLOIC.jar
Ive had different results by lowering the timeout value and increasing the threads. As well as un-checking : Wait For Reply and also HTTP or UDP
By running a ping on the host you can see the response time increasing. Running multiple connections from multiple machine will knock the server off-line.
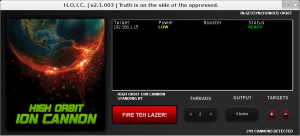
High Orbiting Ion Cannon : Attack from the Cloud
The HOIC is actually an upgrade to an older program, the Low Orbit Ion Cannon, which had been a favored tool of Anonymous and other hacker groups. But the HOIC, which has been around for a little while and is gaining popularity among hackers this year, is much more powerful.
Software Binary : http://sourceforge.net/projects/highorbitioncannon/files/latest/download
Follow the steps below to install High Orbit Ion Cannon into your /opt folder. You need to have wine installed to run it.
My Wine Version info : wine-1.4.1
-
Create Folder in /opt called Hoic : mkdir -p /opt/Hoic
-
Download Rar File into /opt/Hoic
-
Unrar file : unrar e Hoic.rar
-
Start Hoic : wine /opt/Hoic/wine hoic2.1.exe
Usage here is pretty simple. Set the number of threads and hit the Fire Button!! SMH!!!
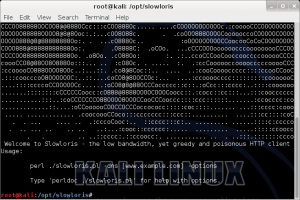
Slowloris : Leave them Doors Open
Slowloris is a piece of software written by Robert “RSnake” Hansen which allows a single machine to take down another machine’s web server with minimal bandwidth and side effects on unrelated services and ports.**
Slowloris tries to keep many connections to the target web server open and hold them open as long as possible. It accomplishes this by opening connections to the target web server and sending a partial request. Periodically, it will send subsequent HTTP headers, adding to—but never completing—the request. Affected servers will keep these connections open, filling their maximum concurrent connection pool, eventually denying additional connection attempts from clients.**
**From Wikipedia : http://en.wikipedia.org/wiki/Slowloris_%28software%29
Software URL : http://ha.ckers.org/slowloris/slowloris.pl
Demo Video :
Installation : Follow the Steps Below to install into your /opt folder.
-
Create Folder in /opt/ called slowloris : mkdir -p /opt/slowloris
-
Wget file to folder : cd /opt/slowloris&&wget http://ha.ckers.org/slowloris/slowloris.pl
-
Set Executable : chmod +x /opt/slowloris/slowloris.pl
-
Run slowloris and look at options : /opt/slowloris/./slowloris.pl
Results with slowloris are quick. Apache quickly climbs to deal with the processes left open. With in seconds the system is not responsive..
Why would Anyone Want to do This?
There are many different reasons why people do this. Not all of them are legal. Sometimes when you design an application or system, you need to test it. DoS Attacks can be used to measure how much load the system will take before it crashes, produces errors to fix, or when it fails to provide the redundancy the systems needs to operate. Other reasons are not so legal. Some times its for fun, for profit, for revenge, and even protesting. Many Different factors contribute to why someone would or wouldn’t want to DDoS attack on the internet. It depends on Motivation. Here are a few of my highlighted reasons….
-
Black markets that exist on the internet shy away from DDoS as it cannot conduct its illegal business model if the internet doesn’t work.
-
One of the Biggest reasons we found is the people that employee this tech have a Territorial Nature or may seek revenge for some feeling of wrong.
-
Sometimes a Bot-Net writer will need to prove the effectiveness of the bot-net, victim may be choose at random, to demo to a prospective sale.
-
DDoS attacks can be Rented as a Service to hurt a competitor during a big on-line sale. Knock Best Buy or Apple off-line for Cyber Monday for example.
-
A fast growing Trend is to use DDoS in Demonstration or Political Statements. Many websites that face DDoS also face Website Defacement, Humiliation, and can even lead to Extortion…
While attacks are growing we can never be certain why someone is getting attacked, but one thing is for sure. People are doing this.
Ive Added some Slides I found doing my research and they have a great illustration for what I found. Ive included them for download here : DDOS Power Point Slides (3335 downloads )






0 comments